Novel approaches to cybersecurity, incubated, tested and accelerated.
Rapid solution development with security by design.
Understanding the threat environment to plan and defend.
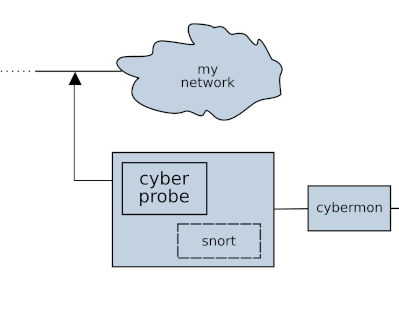
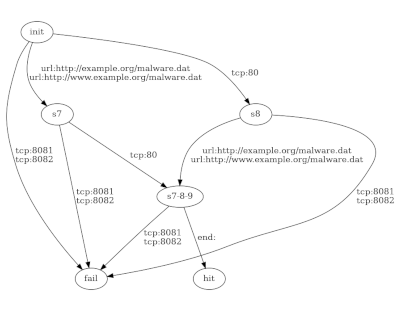
Security detection for advanced threats.
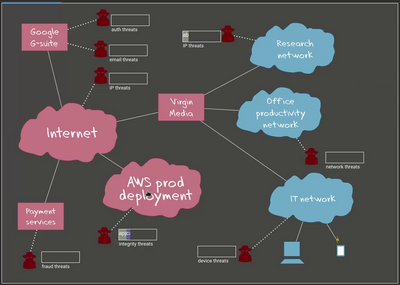
Using business intelligence to unlock detection, there is a wealth of insight on threats and risks sitting undiscovered in every business. Our capability is tailorable to the threat needs of the business and skill levels of security analysts.
The dashboard shows risks as they are tracked in the enterprise. The dashboard dynamically updates as risks are discovered, and can be used by the SOC analyst to jump straight into actionable forensic data.
The Emerging Threats panel discovers new threat seeds and pivots between related threat seeds and forensic information.
The risk model can be tailored to local enterprise risks, and threat information is presented as risk reports which are used to define corporate security strategy and empower executive decisions.
The threat model can be integrated with the detection capability.
The problem with learning to do security engineering on a car's CAN bus is that if you break something (in the spirit of learning), there's 2 tonnes of vehicle which can go out of control. The virtual car was developed for a client to provide a realistic virtual CAN bus for students, which interoperated with existing CAN tools. This was coupled with a physics simulation of the vehicle and engine to make the CAN bus events as realistic as possible. Also included were simulations of the instrument cluster, the ECU and a diagnostic tool.
And, just because we could... the CAN bus messages were modeled on a real car's CAN messages. If we connected the simulated CAN bus out to that car's instrument cluster, the real-world instrument cluster showed the state of the virtual car.
We were commissioned to perform a security review / pen-test on a future EV charger product.
This required reverse-engineering firmware and boot loader and probing internal hardware and software elements as well as executing internal components in an emulator.
EV chargers are emerging technology, but in common with the embedded / IOT ecosystem vendors need to understand the complete supply chain for software and hardware, and establish the patch mechanisms for embedded software. An IOT security review will build the full supply picture and discover any ticking timebombs in your product.
Mainly just for fun, took the commission, to recover documents from a 30-year-old laptop.
Critical CMOS boot data was wiped, very old batteries had failed, and no modern communication ports to transfer data. The real heroes are the people who maintain IBM PS/2 documentation and recovery disks 30 years later.
Anyone for a game of Wolfenstein 3D?
Mapping data to self-describing data forms, ontologies, RDF and SPARQL.
Combined with open-source components results in easy ways to query and navigate linked data.
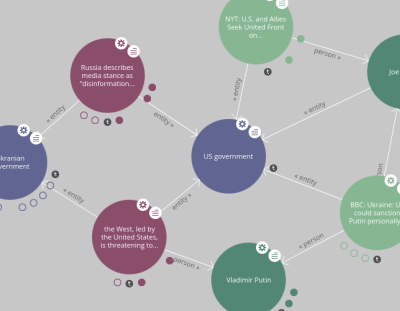
Here's a demo which indexes news articles with related concepts, click on the tiny circles to navigate to related concepts: